With the wide variety of resources available for teachers, there’s no reason we shouldn’t be promoting the importance of behaving safely and responsibly in the digital world. Speaking of resources, check out the nifty infographic shown, one that can be used to address various aspects of digital citizenship.
Learn more:
- https://gustmees.wordpress.com
- https://gustmees.wordpress.com/2015/01/28/practice-learning-to-learn-example-2/
Via Gust MEES



 Your new post is loading...
Your new post is loading...






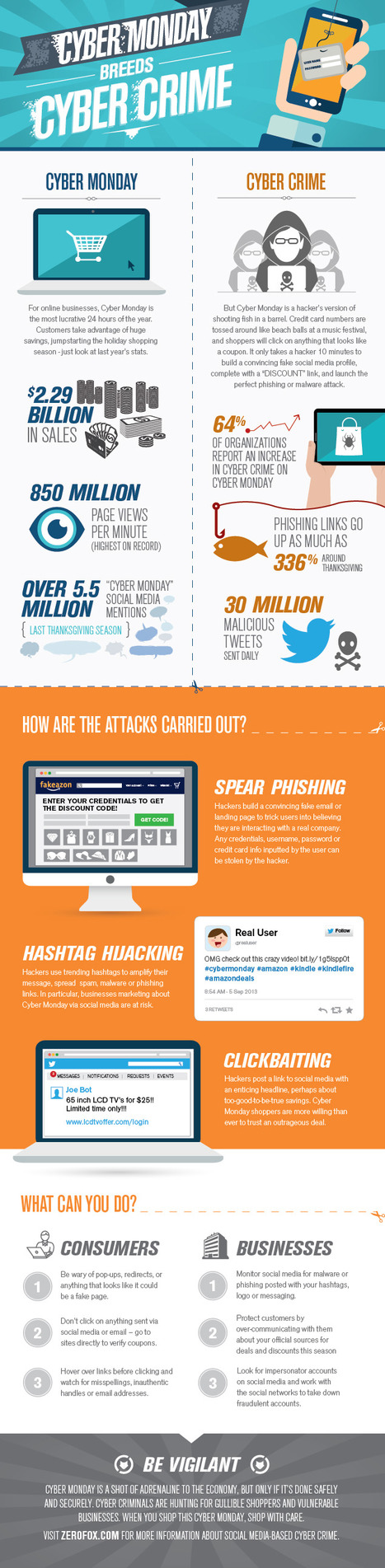
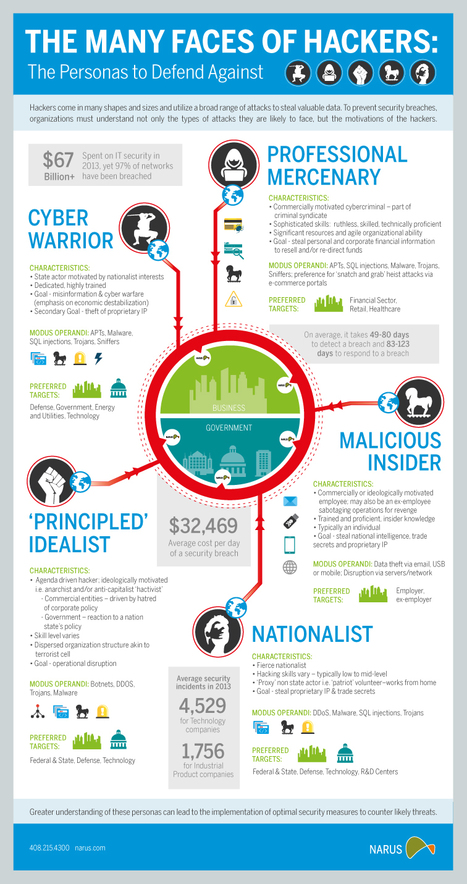



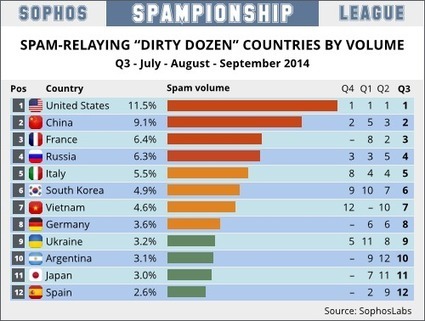


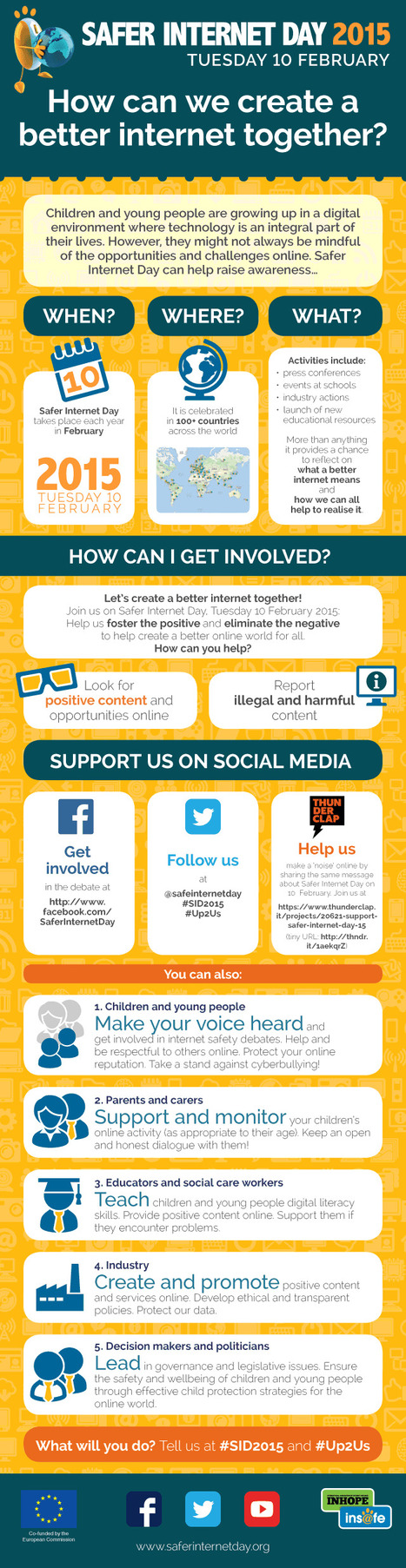




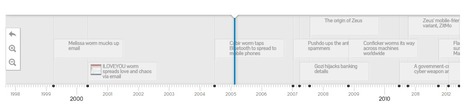




Strength: the design is very creative
Weakness: I don't understand why they represent Spider-Man in this. Also the words are very jammed packed, causing this to look clustered.
Positive: cool topic
negative: a little jumbled & not well organized